
Accelerate your IT roadmap.
Build the best customer experiences with a simple drag-and-drop interface. No more complex code or legacy IT systems.
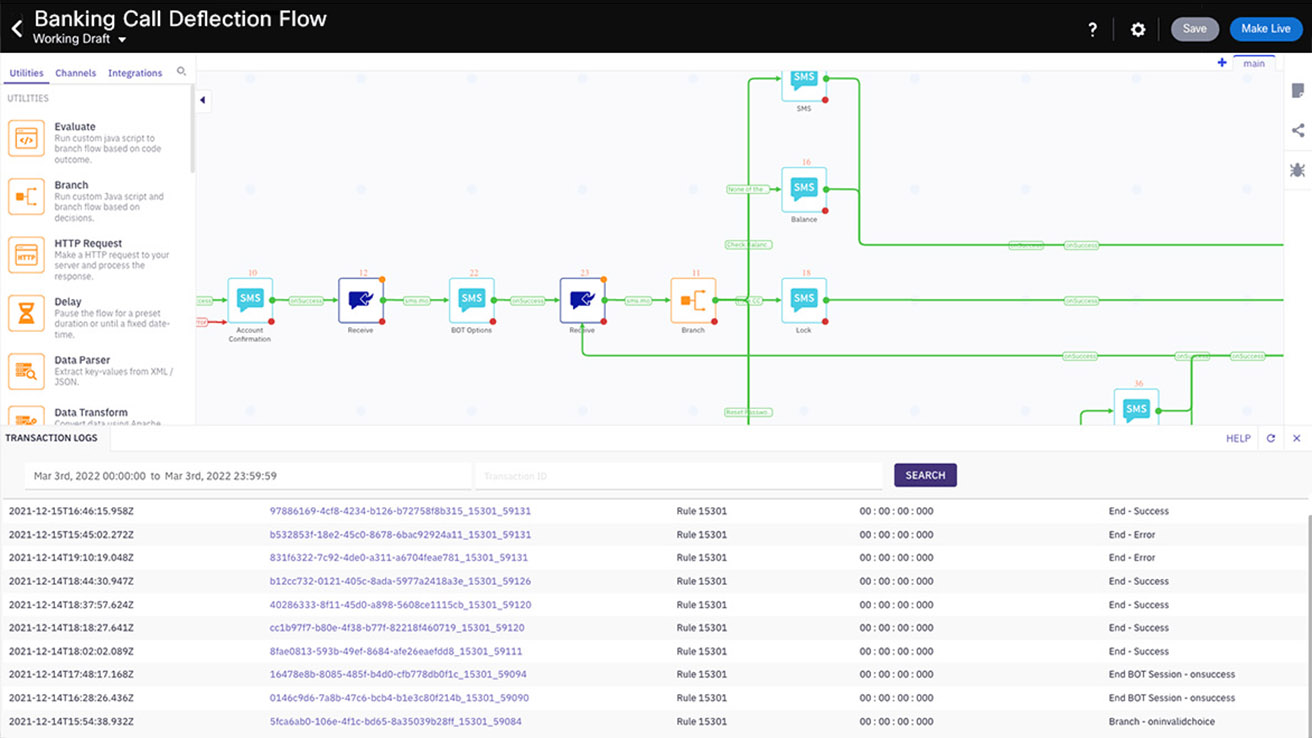
Rapidly build interactive journeys
Flow lifecycle management
Configure, test, deploy, debug, and iterate. Our visual builder provides the tools you need to easily manage the full lifecycle of your customer interactions.
Pre-built components
From social-hour checks and consent management to data persistence and high-speed lookups, leverage the rich set of pre-built nodes to rapidly automate customer interactions.
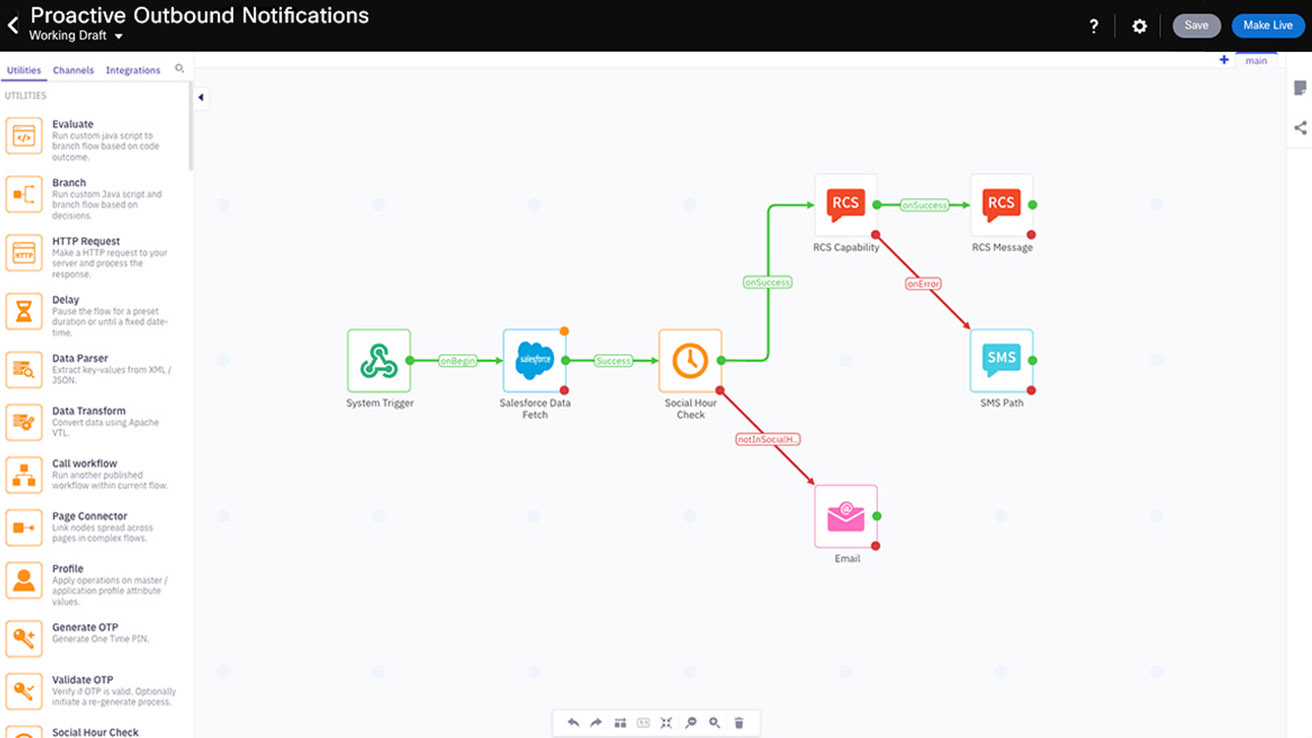
Optimize customer journeys
Break down complexity
Build and iterate complex flows with ease using flow versioning and templates. Add intelligent business logic to track customer preferences and capture data from business systems without writing any code.
Test, analyze, and optimize
Debug flows in real-time with a step-by-step approach. Monitor real-time flow performance using visual analytics and optimize for better outcomes.

Webex Connect whitepaper
Flip through this whitepaper to learn how Webex Connect can help you manage an increasingly complex communications landscape and deliver a differentiated customer experience.
Key features.
-
Built to scale
Keep up with changes in your customer interaction volumes with elastic scalability.
-
Data processing
Convert data from external API calls into a suitable format. Use the integrated database node to store contextual information.
-
Multichannel interactions
With pre-built nodes for 16+ channels, you can leverage the unique capabilities offered by each channel to configure rich customer experiences.
-
Flexible triggers
With a range of options, custom event APIs, webhooks, and file feeds, your backend systems can easily trigger customer interactions without requiring any re-engineering.
-
One-click deployment
Build, test, and deploy communication flows with a single click on a serverless environment.
-
Data security
Encrypt customer data and apply cryptographic hash within flows to securely handle sensitive data such as personally identifiable information (PII).
